
We have a fully-integrated support system built into the Platform through which we can communicate with an individual developer who requests help. We can also accept feedback on the Platform and individual challenges in the Platform from any user through the platform.
In addition, we offer email support to Training Administrators as needed. For more guided learning, developers can utilize our Walkthroughs feature, which provides step-by-step instructions to help them confidently navigate through missions and coding labs.
Yes, all data generated within our training and evaluation platform is fully downloadable by the Training Administrator at any time. This ensures that your organization has continuous access to valuable insights and performance metrics, which can be used for internal reporting, compliance, or further analysis.
Our platform is designed to seamlessly integrate with your existing Learning Management System (LMS), enabling you to streamline secure coding education and track progress alongside other training initiatives. This flexibility allows you to tailor the learning experience to your organization’s specific needs and easily incorporate Secure Code Warrior into your broader training programs.
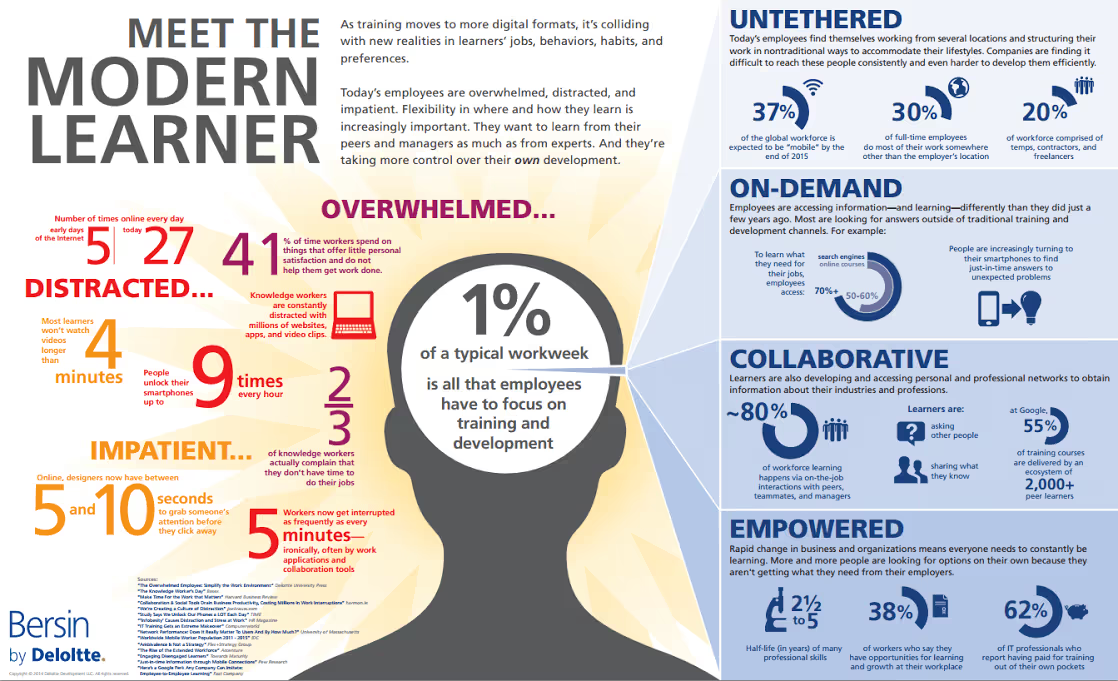
Yes, the training is self-paced. According to Deloitte’s “Meet the Modern Learner,” typically 1% of a typical workweek is all that employees have to focus on training and development. Our platform is built to ensure that this available time is hands-on and effective but it is also designed with the goal that Developers can utilise it outside work hours. On-demand learning in an 'everywhere available' format is critical for today’s learner.
No. We have new developers with little secure code experience and seasoned developers with lots of experience on the platform. For new developers, we have built in Learning and Knowledge Transfer to help them shape their basic skills and understanding of the leading vulnerabilities. As their skills develop and, like seasoned developers, they become more aware they are challenged by the gamified engagement and increasingly difficulty of the content challenges to constantly improve and become a Secure Code Warrior.
We prioritize the security and privacy of customer data by minimizing the storage of any Customer or Personally Identifiable Information (PII) to the greatest extent possible. Customer data is stored securely in our production systems and is retained only as long as necessary—either until you choose to delete it or your license expires and deletion is requested. We follow strict protocols to ensure that your data is protected at all times. For more detailed information, read here for our full data protection policy.
Current software security tools and processes focus on moving from right to left, so called 'shifting left' in the Software Development Life Cycle (SDLC) – an approach that supports detection and reaction – detect the vulnerabilities in the written code and then react to fix them.
Secure Code Warrior takes a different approach by 'starting left' and creating the Secure Software Development Life Cycle (SSDLC). This focus makes the developer the first line of defense in their organization and prevents vulnerabilities in the first place.

Yes, we offer tiered pricing for organizations with 100 or more users. Our pricing structure is designed to accommodate the needs of larger teams, providing greater value as your team size increases. For detailed information on our Business and Enterprise plans, which cater to teams ranging from 50 to 100+ developers, please visit our pricing and packages page. There, you'll discover how each plan is tailored to meet the unique requirements of different-sized businesses, ensuring that your organization can effectively leverage our secure coding platform while benefiting from scalable, cost-effective pricing. Whether you're looking for continuous learning access, in-depth data analytics, or a dedicated customer success manager, we have the right plan to support your team's growth and security needs.
Access to Secure Code Warrior's Learning Platform is offered through flexible annual or multi-year subscriptions, allowing you to choose the term that best fits your organization’s needs. Our user-based pricing model scales with the size and complexity of your AppSec program, ensuring that as your team grows, our platform continues to support your expanding requirements. Whether you're a small team or a large enterprise, our subscription model is designed to provide comprehensive access to secure coding resources that align with your strategic goals.
Our Learning Platform offers robust analytics that track and measure a developer’s progress throughout their secure coding journey. Depending on your account configuration, Administrators, Team Managers, and Developers can monitor a wide range of metrics, including challenges completed, time spent on training, strengths and weaknesses, as well as accuracy and confidence scores. Additionally, Secure Code Warrior offers SCW Trust Score which provides an industry-first benchmark of your secure code learning. These insights empower your team to identify areas for improvement, optimize training efforts, and demonstrate the effectiveness of your AppSec program over time.
Our challenges are continuously revised and updated with new challenges and new language:frameworks to cover new vulnerability types. Right now, we have thousands of challenges in different languages:frameworks covering the OWASP Top 10, OWASP Mobile Top 10, OWASP API Security Top 10, CWE and SANS Top 25. If you don’t see your language:framework of choice, drop us a note.
We’re committed to keeping our content current, so if you don’t see your preferred language or framework, we encourage you to reach out to us. We’re always looking to expand our offerings based on user feedback and evolving industry standards.
Our platform provides an extensive catalog of challenges and missions that cover a wide range of vulnerability types, ensuring comprehensive training for your development team. We address critical security concerns, including the OWASP Top 10, among other industry-recognized threat categories. To learn more about the specific vulnerabilities we cover, and how they align with your organization’s security needs, you can explore further details here.